If MIM fails to install with the error:
Calling custom action Microsoft.IdentityManagement.ServerCustomActions!Microsoft.IdentityManagement.ServerCustomActions.CustomActions.AddServiceToPerformanceMonitors
Adding FIMService account to ‘Performance Monitor Users’ group
Property name = ‘ServiceAccount’, value = ‘XXXXX\XXXXX$’.
DomainName=’XXXXX’
AccountName=’XXXXX$’
Domain AD found
Exception thrown by custom action:
System.Reflection.TargetInvocationException: Exception has been thrown by the target of an invocation. —> System.UnauthorizedAccessException: Access is denied.
Check your domain controllers for the following error in the event log
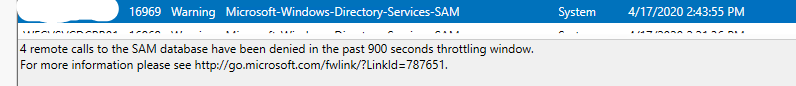
This is due to Network access: Restrict clients allowed to make remote calls to SAM being set on the domain controllers.
In case anyone else stumbles upon this and is not permitted to completely disable the policy mentioned here….
Adding the MIM Service and\or the MIM Install account to the list will NOT solve the problem.
I read through the provided link about the network access restriction policy and noticed the Audit Mode. I enabled the audit mode on the 2 DCs in the client Dev lab where I was having the issue. The audit entries came up with a different account SID than both of the user accounts.
Turns out it is the Computer account of the system in which MIM Service is being installed on that performs the query to the DCs.
In case anyone else runs into this and can’t\won’t completely disable this policy….
I tried adding both the MIM Service and MIM Install accounts to the policy, however it made no difference.
After reading through the posted link about the policy I noticed the Audit Mode. It will log entries that would fail, if the policy is enabled. However Audit Mode prevents the failures from happening, only logs that they would have failed.
After enabling the Audit Mode, I discovered that the account SID in the warning entries in the System event log did not match the account SIDs displayed in the policy setting for the MIM Install or MIM Service accounts.
It turns out that SID in the log is the SID of the computer object that MIM Service is being installed on. Adding
Hi Stephen,
We’re facing a similar case in our environment. We have tried adding the installer account to Domain Admins and have also modified the GPO to allow the account SAM calls but with no avail. Is there any solution/workaround for that issue? (we’d like to leave the GPO applied to DCs for now)
Kind regards,
Alek
Ok, I can answer myself. After some troubleshooting of events on Domain Controllers (event ID 16965) it turned out, that the SAM calls were triggered by Computer account (MIM Service/Portal server), not by User account (MIM installer). We added the proper Computer accounts to the allowed group in GPO configuration and the Service/Portal installation process finished successfully.
Kind regards,
Alek